- Apache Http Strict-transport-security Header
- Apache Disable Http Strict Transport Security
- Http Strict Transport Security 設定 Apache
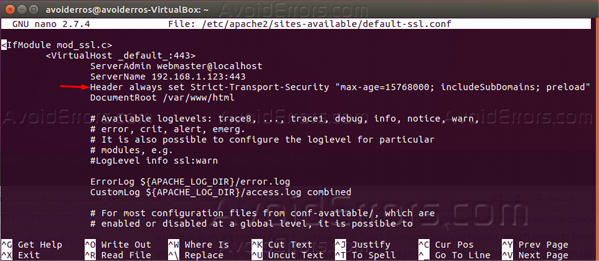
I would like to add HTTP Strict Transport Security directive to my.htaccess file. I've added the lock at the end of the code here but when I test Testing the HSTS preload process it show the setting not set. I checked my Apache config and see the headers module enabled. What am I missing? Apache - Configuring HTTP Strict Transport Security To configure the Apache webserver to use HTTP Strict Transport Security (HSTS), the following steps can be taken. How to Setup HTTP Strict Transport Security (HSTS) for Apache by Vikas Munjal September 19, 2017 HTTP Strict Transport Security, widely known as HSTS, is a web security policy mechanism in which website tells the browser that it should only be communicated using HTTPS, instead of using HTTP Protocol. HSTS or HTTP Strict Transport Security provides an extra layer of security for HTTPS (SSL / TLS) traffic by preventing the connection to be downgraded to HTTP, which is not encrypted. HSTS can be enabled in Apache by enabling the headers module with some specific configurations. Steps to enable HSTS on Apache.
Apache Zeppelin can be configured to include HTTP Headers which aids in preventing Cross Site Scripting (XSS), Cross-Frame Scripting (XFS) and also enforces HTTP Strict Transport Security. Apache Zeppelin also has configuration available to set the Application Server Version to desired value.
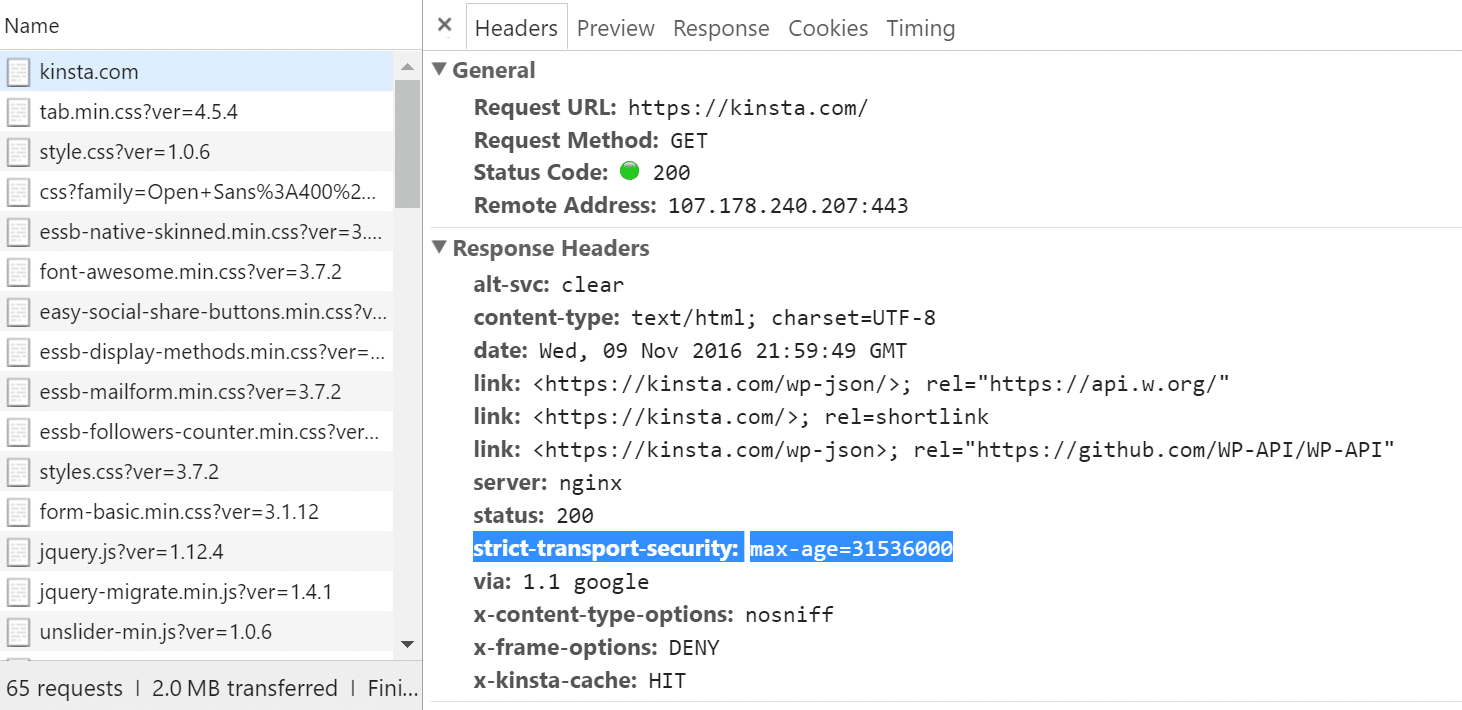
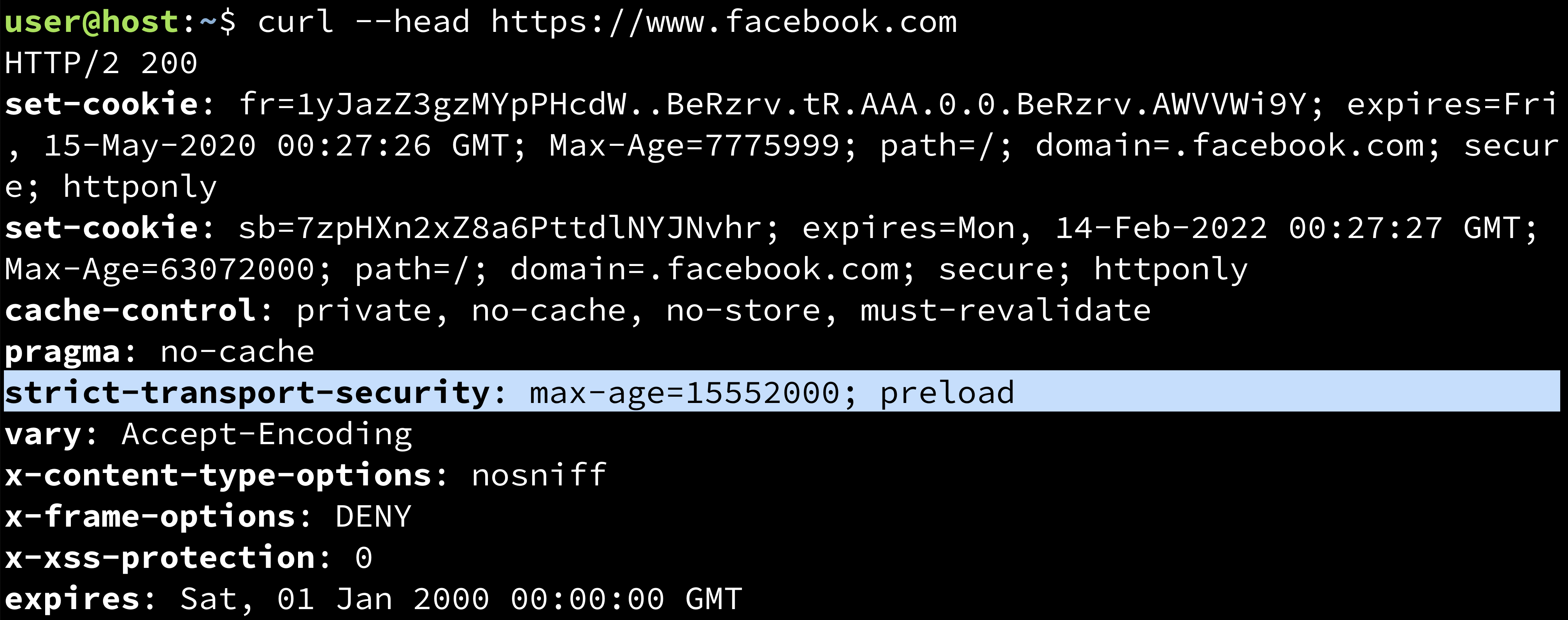
Setting up HTTP Strict Transport Security (HSTS) Response Header
Enabling HSTS Response Header prevents Man-in-the-middle attacks by automatically redirecting HTTP requests to HTTPS when Zeppelin Server is running on SSL. Read on how to configure SSL for Zeppelin here. Even if web page contains any resource which gets served over HTTP or any HTTP links, it will automatically be redirected to HTTPS for the target domain. It also prevents MITM attack by not allowing User to override the invalid certificate message, when Attacker presents invalid SSL certificate to the User.
The following property needs to be updated in the zeppelin-site.xml in order to enable HSTS. You can choose appropriate value for 'max-age'.
Possible values are:
- max-age=<expire-time>
- max-age=<expire-time>; includeSubDomains
- max-age=<expire-time>; preload
Read more about HSTS here.
Setting up X-XSS-PROTECTION Header
The HTTP X-XSS-Protection response header is a feature of Internet Explorer, Chrome and Safari Web browsers that initiates configured action when they detect reflected cross-site scripting (XSS) attacks.
The following property needs to be updated in the zeppelin-site.xml in order to set X-XSS-PROTECTION header.
You can choose appropriate value from below.
- 0 (Disables XSS filtering)
- 1 (Enables XSS filtering. If a cross-site scripting attack is detected, the browser will sanitize the page.)
- 1; mode=block (Enables XSS filtering. The browser will prevent rendering of the page if an attack is detected.)
Read more about HTTP X-XSS-Protection response header here.
Setting up X-Frame-Options Header
The X-Frame-Options HTTP response header can indicate browser to avoid clickjacking attacks, by ensuring that their content is not embedded into other sites in a <frame>,<iframe> or <object>.
The following property needs to be updated in the zeppelin-site.xml in order to set X-Frame-Options header.
You can choose appropriate value from below.
DENYSAMEORIGINALLOW-FROM uri
Apache Http Strict-transport-security Header
Setting up Server Header

Security conscious organisations does not want to reveal the Application Server name and version to prevent finding this information easily by Attacker while fingerprinting the Application. The exact version number can tell an Attacker if the current Application Server is patched for or vulnerable to certain publicly known CVE associated to it.
Apache Disable Http Strict Transport Security
The following property needs to be updated in the zeppelin-site.xml in order to set Server header.
Http Strict Transport Security 設定 Apache
The value can be any 'String'.
